


Cross Site "Scripter" (aka XSSer) is an automatic -framework- to detect, exploit and report XSS vulnerabilities in web-based applications.
It provides several options to try to bypass certain filters and various special techniques for code injection.
----------
XSSer has pre-installed [ > 1300 ] XSS attacking/fuzzing vectors and can bypass-exploit code on several browsers/WAFs:
- [PHPIDS]: PHP-IDS
- [Imperva]: Imperva Incapsula WAF
- [WebKnight]: WebKnight WAF
- [F5]: F5 Big IP WAF
- [Barracuda]: Barracuda WAF
- [ModSec]: Mod-Security
- [QuickDF]: QuickDefense
- [Sucuri]: SucuriWAF
- [Chrome]: Google Chrome
- [IE]: Internet Explorer
- [FF]: Mozilla's Gecko rendering engine, used by Firefox/Iceweasel
- [NS-IE]: Netscape in IE rendering engine mode
- [NS-G]: Netscape in the Gecko rendering engine mode
- [Opera]: Opera Browser
 |
wget https://xsser.03c8.net/xsser/xsser_1.8-3.tar.gz
tar xf xsser_1.8-3.tar.gz
cd xsser
sudo python setup.py install
./xsser -h
./xsser --gtk (for gui)
URL/Hash Generation Schema: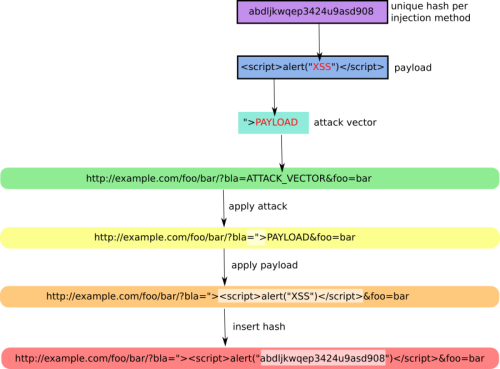 +Zoom |
Shell: +Zoom |
Manifesto: +Zoom |
Configuration: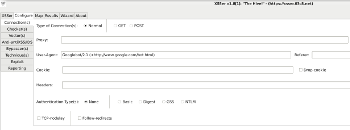 +Zoom |
Bypassers: +Zoom |
GeoMap: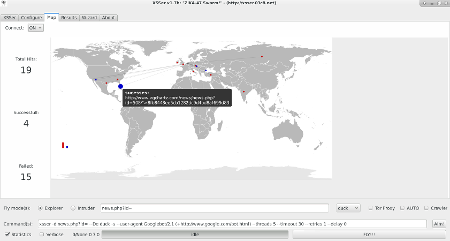 +Zoom |
[HTTP GET] [LOCAL] Reverse Exploit: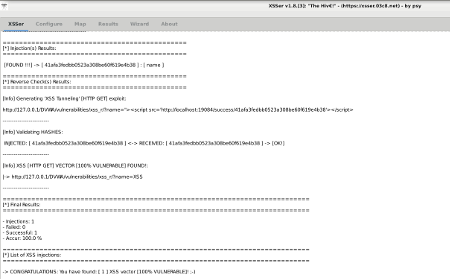 +Zoom |
[HTTP POST] [REMOTE] Reverse Exploit: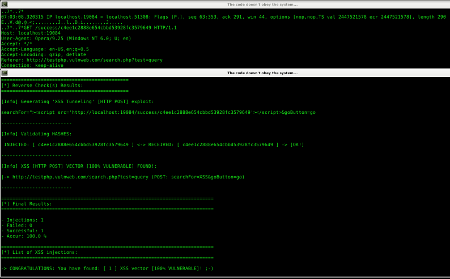 +Zoom |
[XSS DOM] Exploit: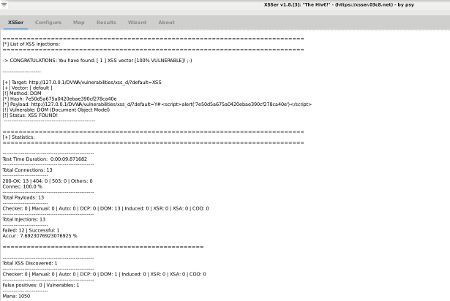 +Zoom |
XSSer runs on many platforms. It requires Python (3.x.y) and the following libraries:
You can automatically get all required libraries using (as root):
sudo python setup.py install (or sudo python3 setup.py install)
For manual installation on Debian-based systems (ex: Ubuntu), run:
sudo apt-get install python3-pycurl python3-bs4 python3-geoip python3-cairocffi python3-selenium firefoxdriver
On other systems such as: Kali, Ubuntu, ArchLinux, ParrotSec, Fedora, etc... also run:
sudo pip3 install pycurl bs4 pygeoip gobject cairocffi selenium
ex: git clone https://code.03c8.net/epsylon/xsser
ex: git clone https://github.com/epsylon/xsser
XSSer v1.8.3: "The HiV€!" :
wget https://xsser.03c8.net/xsser/xsser_1.8.3_all.deb
sudo dpkg -i xsser_1.8.3_all.deb
xsser -h
xsser --gtk (for gui)
XSSer v1.8.2: "The Hiv3 (beta)!" -> * XSSer is ported to Python3:
XSSer v1.7.2b: "ZiKA-47 Swarm!":
XSSer v1.6: "Grey Swarm!":
XSSer v1.5: "Swarm Edition!":
XSSer v1.0: "The mosquito":
XSSer is released under the terms of the General Public License v3 and is copyrighted by psy.
This framework is actively looking for new sponsors and funding. If you or your organization has an interest in keeping XSSer, please contact directly.
For donations: